Do you know that a few good guys use their skills to protect us from cyber threats? They are the red hat hackers! These are tech-savvy good guys fighting against the world of online crime.
Basically, these are computer experts. They use their skills willingly to help and protect us against cyber threats. Black hat hackers cause damage, while red hat hackers work to fix security issues and stop cybercrime. They team up with companies to keep our online world safe for everyone.
This blog explores the concept of red hat hackers, their role, legality, and impact on cybersecurity. Let’s get started!
What is a Red Hat hacker?
In the world of cybersecurity, red hat hackers are special and debatable types of hackers. They are also known as “vigilante hackers.” A red hat hacker is a person who utilizes their expertise in hacking to spread a message while also acting as a digital activist.
Characteristics of red hat hackers:
- These types of hackers' target Linux systems
- They may hack for ideological, religious, social, or political purposes.
- They put their expertise and abilities to good use.
- They take a strong and proactive strategy in their fight against cyber threats.
- Their main goal is to defend users and systems that are at risk from additional threats.
Role of Red Hat Hackers in Cybersecurity:
Red hat Hackers are the good folks in cybersecurity who help keep bad guys out of networks. To accomplish this, they aggressively search for flaws in networks and software, perhaps employing strategies that actual hackers would use.
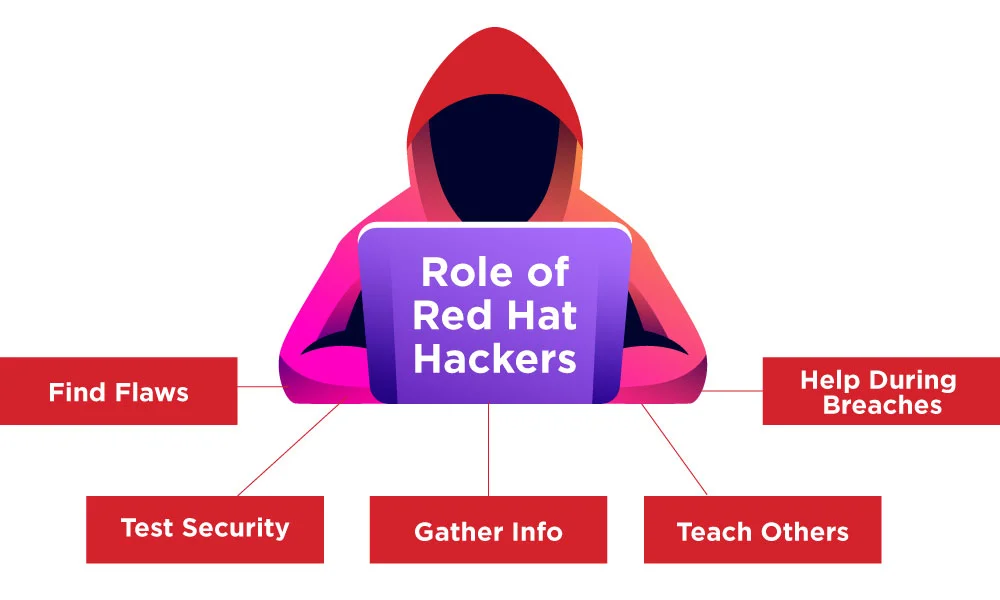
This is what they usually do:
- Find Flaws: They look for security flaws that hackers may abuse.
- Test Security: They conduct imaginary crimes to test a system's resilience, assisting corporations in identifying their vulnerabilities.
- Gather Info: They assess any dangers and spread their knowledge to keep others safe.
- Teach Others: They frequently share their research results to assist security teams in improving their defenses against cyberattacks.
- Help During Breaches: Red hat hackers have the ability to look into the hack and assist in resolving the problems if an organization is hijacked.
Legality of Red Hat Hackers
The legal context in which red hat hackers operate is complex. In contrast to black hat hackers, they seek to strengthen security and typically receive authorization from the companies they collaborate with, which ensures that their activities are lawful. However, if their aggressive tactics are thought to be invasive, they may occasionally cause miscommunications or legal problems.
They must get agreements that specify their area of service and adhere to certain criteria to be safe. Effective communication with organizations is crucial to prevent misunderstandings. Ultimately, even if they want to improve security, they have to carefully tread legal lines to make sure their actions are morally and legally acceptable.
Impact of Red Hat Hackers on Cybersecurity
Red hat hackers significantly improve cybersecurity in the following ways:
- Identifying Vulnerabilities: To assist enterprises in addressing system vulnerabilities before harmful hackers may take advantage of them, they actively look for them.
- Simulating Attacks: They give businesses insights into possible attack techniques by simulating actual hacking scenarios, enabling them to enhance their defenses.
- Raising Awareness: By exchanging research results and best practices, they train security staff and promote a security-conscious culture inside businesses.
- Improving Tools and Technologies: Their practical testing might uncover vulnerabilities in security tools and software that could otherwise go undetected, resulting in more potent remedies.
- Contributing to a Secure Internet: Red hat hackers assist in lowering the overall threat of cybercrime by safeguarding specific companies, which benefits everyone on the Internet.
Conclusion
Red hat hackers are good people for cybersecurity. They work hard to find and fix security issues, helping keep our online world safe. By sharing their knowledge and skills, they not only protect companies but also promote a culture of safety for all. Their efforts make the internet a better and safer place for everyone.
We hope our efforts in explaining this concept will help our readers. To understand more such elements, visit us at KnowledgeNile.
Read More:
5 Reasons Why Digital Marketing is Crucial for Your Business